SINGAPORE - Top US fuel pipeline operator Colonial Pipeline is working around the clock to overcome a paralysing cyber attack, one of the most serious energy-sector hacks in history.
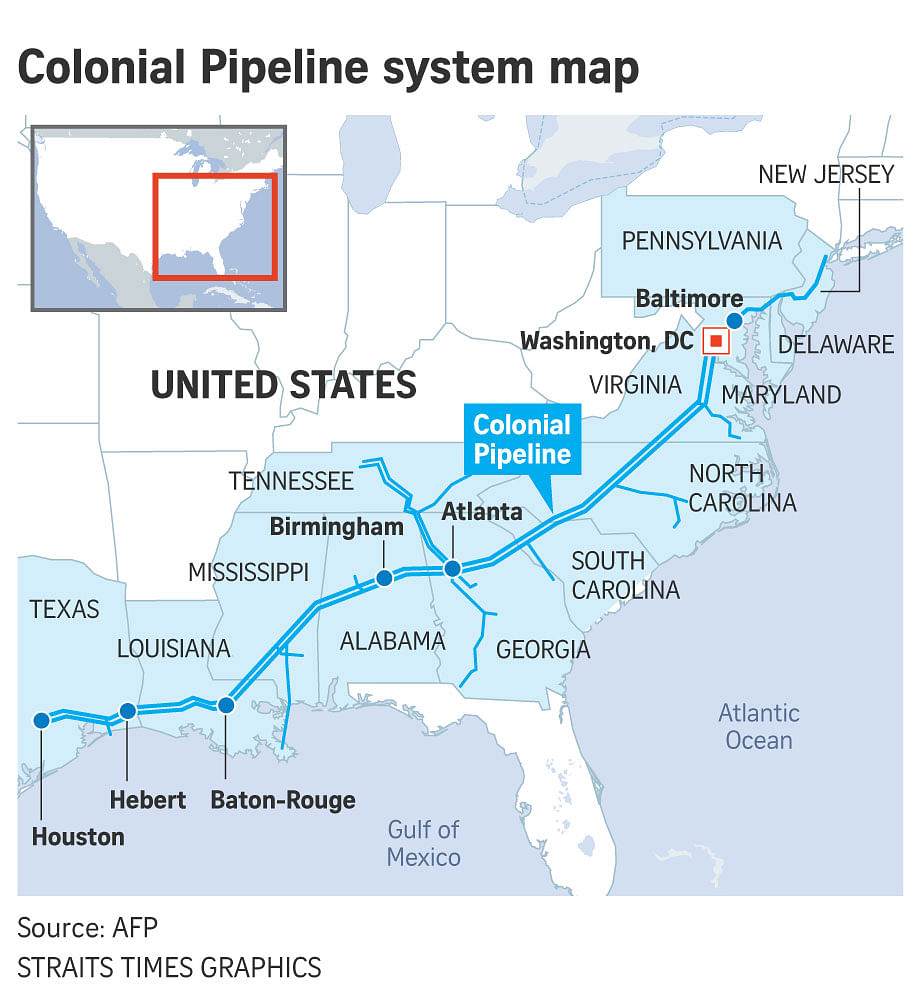
Colonial transports about 45 per cent of all fuel consumed on the east coast of the United States and any delay in restarting supply may cause pump prices to rise.
The pipeline also serves 90 US military installations and 26 oil refineries, according to Bloomberg.
Here is what we know about the hack last Friday and the group behind it.
Can a pipeline be hacked?
Yes. Beyond physical pipes and pumps with greasy black liquid flowing through it, the entire network is run by sophisticated computers that are connected to a central system to monitor and control a wide array of sensors, valves and leak-detection tools.
"All the devices used to run a modern pipeline are controlled by computers, rather than being controlled physically by people," cyber security expert Jon Niccolls told the BBC.
"If they are connected to an organisation's internal network and it gets hit with a cyber attack, then the pipeline itself is vulnerable to malicious attacks."
How did the hack occur?
The FBI said a hacking group known as DarkSide was responsible. The hackers stole nearly 100GB of data before locking up computers with ransomware and demanding payment.
Both Colonial and federal officials have not explained how the breach occurred.
The New York Times (NYT) quoted federal officers and private investigators as saying that the ransomware was not directed at the control systems of the pipeline, but rather the back-office operations of Colonial.
The company has shut down its system to prevent further damage.
Investigators subsequently found the stolen data stored in US-based servers, which were subsequently disabled by the authorities. As a result, Colonial managed to recover some of the data.
Investigators believed the data's ultimate destination was Russia, according to three people Bloomberg spoke to who had knowledge of the matter.
Cyber security experts said Colonial's system was vulnerable enough for the hackers to gain access. A preliminary investigation showed poor security practices at Colonial, NYT reported. The lapses most likely made the act of breaking into and locking up the company's systems fairly easy.
What is known of DarkSide?
The group, which came to prominence in August 2020, is believed to be based either in Russia or Eastern Europe.
Ms Anne Neuberger, US deputy national security adviser for cyber and emerging technology, described it as a "criminal actor" that hires out its services to the highest bidder, and then shares "the proceeds with ransomware developers".
Based on previous incidents, DarkSide has demanded ransoms between US$200,000 (S$265,300) and US$2 million.
Global technology company Acronis said DarkSide targets only English-speaking countries while avoiding former Soviet countries, leading to widespread belief that it is somewhat linked to Russia.
The group has depicted itself as some sort of online Robin Hood - extorting from corporations and donating some of its gains to charities.
What's next?
Colonial said it expects to restore all service by the weekend but that may not be fast enough. There are already reports of petrol stations along the East Coast running out of fuel.
The incident underscores the vulnerability of the US' critical infrastructure, especially its energy sector.
IBM Security's annual X-Force Threat Intelligence Index ranked energy as the third most-attacked industry in 2020, up from ninth place the year before.
"This most recent hit by hackers underscores how the utility industry needs to recognise that there is a link between their information technology systems and their operational technology that is directly connected to the grid," Mr Tobias Whitney, vice-president of energy security solutions for Fortress Information Security, told Bloomberg.
"Everyone involved with critical infrastructure will want to understand how this happened and learn how to prevent it from occurring on their systems in the future," he said.


